In a previous blog post, we discussed the signing of documents with tokens and proposed a simple tool to check the content of a PKCS#11 token. We also introduced digital signatures, X509, ASN.1, CMS, PDF and ETSI standards for signatures.
In this post, we simply introduce a 'proof of concept' application to sign and verify PDFs with PKCS#11 tokens: PDFSignVerify. The application is a proof of concept (PoC) because it is not possible to address all PDF versions and formats in a simple tool. Addressing all cases would resort to developing a complex app that is way beyond the scope of a cryptographic library.
Portable Document Format (PDF)
PDF specifications are laid out in an ISO standard [1]. Signatures can be added to PDF files in the form of Cryptographic Message Syntax (CMS) sequences [2] coded in ASN.1 DER (see aforementioned post). Our PDFSignVerify PoC uses the ETSI EN 319 141-1 and 141-2 standards [3]. In particular, as TMS Cryptography Pack doesn't support SHA1 for new signatures, we use the ESS signing-certificate-v2 attribute in the Signed Attribute sequence.
The Signed Attribute sequence is defined like this:
id-aa-signingCertificateV2 OBJECT IDENTIFIER ::= { iso(1)
member-body(2) us(840) rsadsi(113549) pkcs(1) pkcs9(9)
smime(16) id-aa(2) 47 }
SigningCertificateV2 ::= SEQUENCE {
certs SEQUENCE OF ESSCertIDv2,
policies SEQUENCE OF PolicyInformation OPTIONAL
}
ESSCertIDv2 ::= SEQUENCE {
hashAlgorithm AlgorithmIdentifier
DEFAULT {algorithm id-sha256},
certHash Hash,
issuerSerial IssuerSerial OPTIONAL
}
Hash ::= OCTET STRING
IssuerSerial ::= SEQUENCE {
issuer GeneralNames,
serialNumber CertificateSerialNumber
}The signature is applied to the ASN.1 encoding of the entire sequence and added to the CMS sequence, together with the message digest of the intial PDF file prepared according to section 12.8 of the ISO standard.
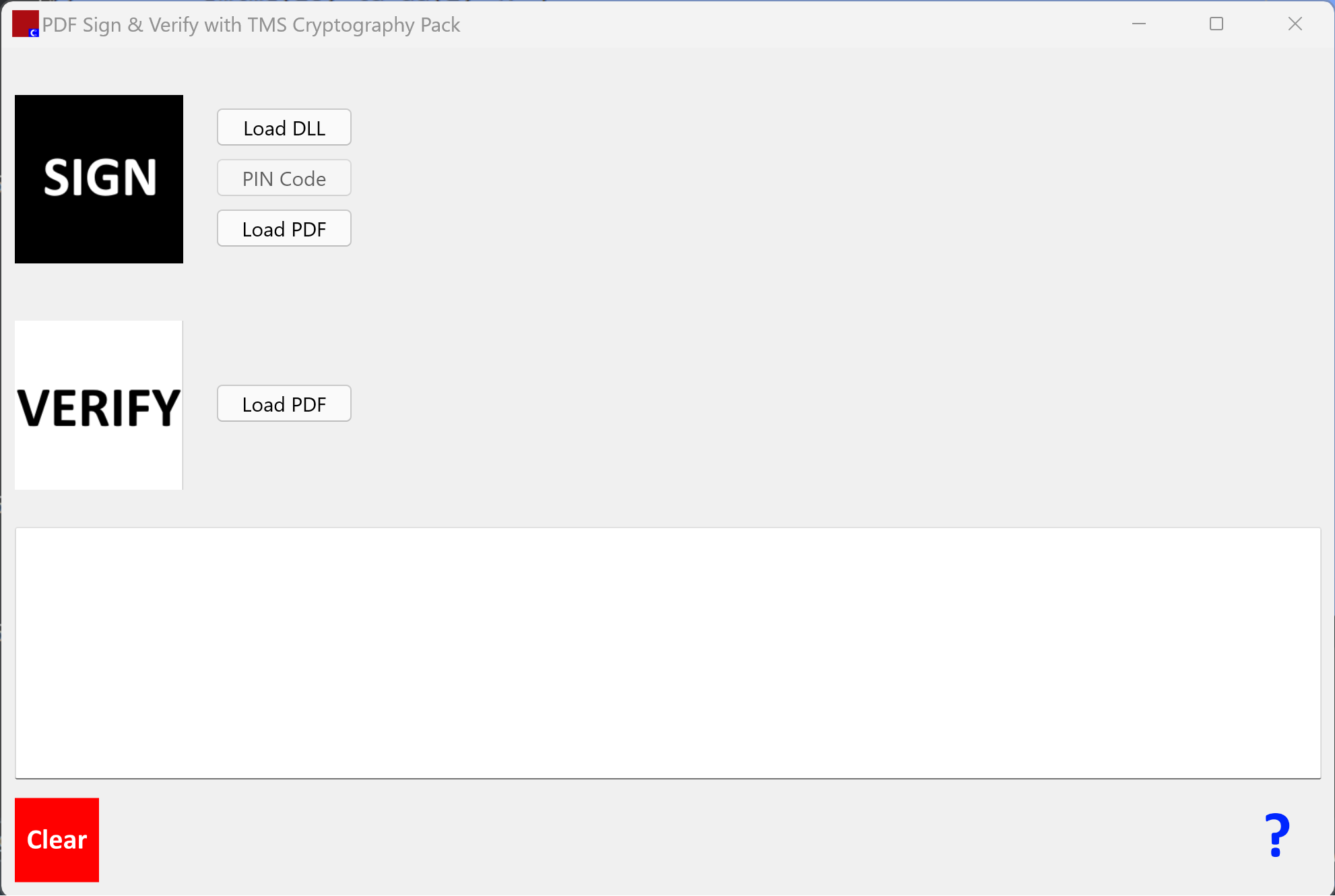
Using the application
The PoC app is very simple with Sign and Verify buttons that can be used once the PKCS#11 driver, the token password and the file to sign (or to verify) have been selected. The 'question mark' button gives access to the 'manual' for the app.
Conclusion
PDFSignVerify has been developed with TMS Cryptography Pack version 5.0 that will be issued in a few weeks. This version if fully written in Pascal Object and is currently being finalized with new classes but also with the deletion of deprecated algorithms, such as RIPEMD160.
The new PDF signatures have been successfully tested for interoperability with Adobe Acrobat Reader, FoxIT PDF Reader, PDF X-Change Editor and Microsoft Edge. However, PDF has many variants and signatures may not be recognized for all versions and flavours.
PDFSignVerify is free of use.
P.S.: feel free to report any issues to the Author via the TMS Cryptography Pack support page or directly by email
[1] ISO 32000-2:2020, Document Management, Portable Document Format (PDF)
[2] Cryptographic Message Syntax (CMS), RFC 5652, https://datatracker.ietf.org/doc/html/rfc5652
[3] ETSI EN 319 141-1 and 141-2, Electronic Signatures and Infrastructures (ESI), PAdES digital signatures